The reality is, if you think all VPNs are created equal, you’re headed for a headache—and maybe a breach or two. Whether you’re a busy IT manager or a security analyst on a never-ending firefight, the difference between SSL VPN and IPsec isn’t just academic; it matters. Because screw-ups here cause real-world damage. Ransomware outbreaks, leaks, unauthorized access… you name it.
You know what’s funny? Despite half-decent marketing from big names like SonicWall, Ivanti, and Check Point Software, VPN protocols are routinely misunderstood or misconfigured—especially when admins slap on default settings and “set it and forget it.” The end result? Over-permissive rules that throw open the digital front door for threat actors to stroll right in.

Types of VPN Protocols: SSL VPN vs IPsec — Why Should You Care?
Let’s start with the basics, stripped of all buzzwords and fluff:
- IPsec VPNs (Internet Protocol Security) operate at the network layer, securing all traffic between two networks or a client and network by creating encrypted tunnels. Think of it as a virtual, encrypted pipe connecting two endpoints, no matter what’s inside the pipe. SSL VPNs (Secure Sockets Layer), on the other hand, work at the transport layer and often allow more granular access to specific apps or services, typically over standard HTTPS ports (443). SSL VPNs usually require just a browser or minimal client installation, which makes them more user-friendly in some scenarios.
So, which VPN protocol is best depends on your use case, but don’t be lulled into complacency—every option comes with trade-offs.
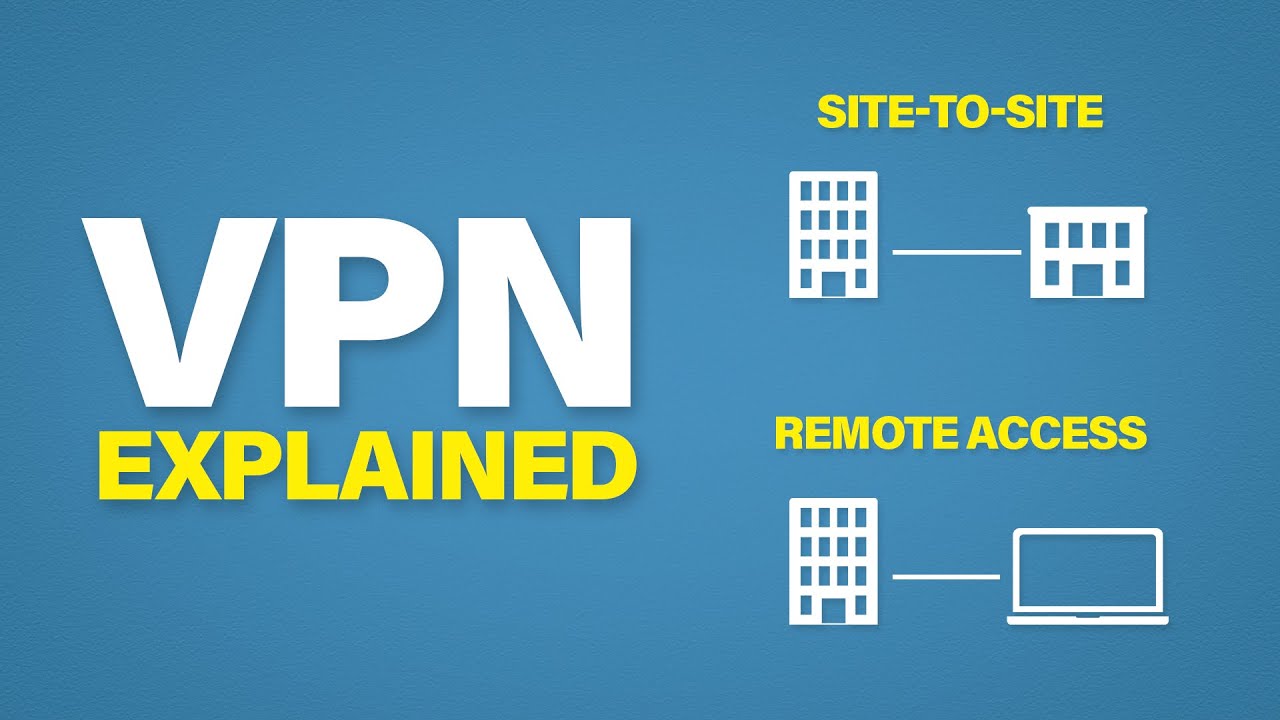
How IPsec VPNs Work
IPsec VPNs set up a secure tunnel by authenticating and encrypting all IP packets exchanged between devices. That’s great for site-to-site VPNs—like linking branch offices to a corporate data center—or remote access where the user needs full network access.
Pro Tip: SonicWall and Check Point Software both have robust implementations of IPsec VPNs, but default configurations often allow broad network access, sometimes too broad.
How SSL VPNs Work
SSL VPNs use the same encryption technology underpinning secure websites. They enable secure remote access to specific applications or desktops without exposing the entire network. Ivanti’s SSL VPN solutions often highlight ease of use and quicker deployment.
Since SSL VPNs tunnel application traffic, they can better enforce access control https://cybersecuritynews.com/corporate-vpn-misconfigurations-major-breaches-caused-by-small-errors/ policies and reduce risk. But—here’s the kicker—they also depend heavily on proper setup. One slip-up, like an over-permissive rule, and you’re back to square one.
The Danger of Simple VPN Configuration Errors: Over-Permissive Rules
Ever notice how the phrase “over-permissive rules” appears whenever a VPN breach hits the headlines? It’s not a coincidence.
- Default settings favor convenience over security. Many network appliances ship with broad rules that let traffic flow wildly. Admins often avoid the tedious task of tightening rules. They think “it works” and don't want to break something by restricting access. “Allow all” policies make it easy for attackers. If malware or ransomware manages to get a foothold, these rules give it a highway to move laterally.
A quick digression from real life: When I was cleaning up a mid-sized manufacturer’s incident last year, their SonicWall IPsec VPN was wide open internally—default network ranges and wildcard masks allowed anyone connected via VPN to hit every server in their corporate network.
Result? The ransomware encrypted their file servers in less than an hour after the initial intruder came in through a compromised user laptop.
Real-World Consequences of VPN Misconfigurations
VPNs should protect your remote workers and branch offices, not become a breach vector themselves. Misconfigured VPNs have enabled some of the worst cyberattacks in recent memory.
Ransomware Infections: Attackers exploit over-permissive rules to spread ransomware laterally once they gain VPN access. Data Leaks: Without granular access control (like SSL VPNs provide), attackers can scoop up sensitive data across your network. Credential Theft Amplification: VPNs with weak authentication combined with default credentials are an open invitation for hackers.Tools like Incogni show how threat actors capitalize on these weaknesses by hunting exposed credentials and improper VPN access logs.
The Enduring Conflict: Security vs Usability in IT
Here’s the rub: Users hate hurdles. They want quick access without jumping through hoops. IT wants solid security. SSL VPNs try to bridge that gap by focusing on application-level access instead of “everything behind the VPN.”
But that’s not a free pass. Misconfigured SSL VPNs can be just as dangerous. If your rules don’t align with least privilege principles, you’ve got a problem.
And IPsec VPNs? Their broad network access can either be a blessing or a curse. The takeaway is about balance. Neither protocol is some magical bullet—your team has to know what they’re doing.
The Risk of Using Default Settings on Network Appliances
Every seasoned pro will tell you to never leave defaults in place, yet it happens constantly.
- Default credentials: Don't let this sink you. Most routers, firewalls, and VPN concentrators come with “admin/admin” or similar creds out of the box. Change them immediately. Default firewall and VPN rules: Vendors like Check Point Software offer default configurations intended for quick starts, but not production. Review them carefully. Default encryption settings: Old and weak algorithms leave you exposed.
Skipping these steps turns your "secure" VPN into a sitting duck. Don't be that admin who wakes up to a scream from the help desk because encryption keys were never rotated or firewall rules never tightened.
Comparison Table: SSL VPN vs IPsec VPN
Feature SSL VPN IPsec VPN Protocol Layer Transport Layer (SSL/TLS) Network Layer Use Cases Application-level access; remote desktop, web apps Full network access; site-to-site, remote network access Client Requirements Browser-based or lightweight client Dedicated VPN clients Setup Complexity Generally simpler, easier rollout More complex, especially for site-to-site Access Control Granularity High (app-specific) Lower (network-wide access) Common Vendors Ivanti, Check Point SSL SonicWall, Check Point IPsecSo What’s the Takeaway Here?
Understanding the ssl vpn vs ipsec debate isn’t just about the “which VPN protocol is best” marketing question. It’s about knowing how each fits into your network defense strategy—and how the smallest oversight can cause the biggest disaster.
- Don’t rely on default settings. Change credentials, tighten firewall and VPN access rules, and audit regularly. Know your use case. Need full network access? IPsec might be your go-to. Need selective app access without heavy client installs? SSL VPN could be better. Watch out for over-permissive rules—they’re the silent door flingers that let ransomware and attackers in. Balance security with usability through careful planning, testing, and policies—yes, it takes effort, but it beats incident response costs.
In the end, VPNs are a critical piece of your organization's security fabric, but they’ve got to be deployed wisely. Otherwise, all your fancy tools—from Incogni to enterprise-grade firewalls—won't matter.
And remember: The next time you grab that cup of black coffee and fire up your management console, double-check those VPN configs before your users find a way to bring the whole network down.